The Hidden Dangers of Business Email in 2025
Email remains a vital tool for business communication. But in 2025, it’s also a growing target for cybercriminals. From phishing scams to AI-powered fraud, threats are evolving fast. Let’s explore what business users need to watch out for—and how to stay safe.
Click on the headers below to find out more about email Inbox threats. Click on inmages to view at full-sized resolution.
Phishing Scams: Smarter, Sharper, and More Targeted
Phishing is no longer about mass emails with poor grammar. Today’s scams are precise and convincing. Attackers use generative AI to craft messages that mimic real people and companies according to Threatlabz. These emails often target HR, finance, and payroll teams—where sensitive data and money flow.
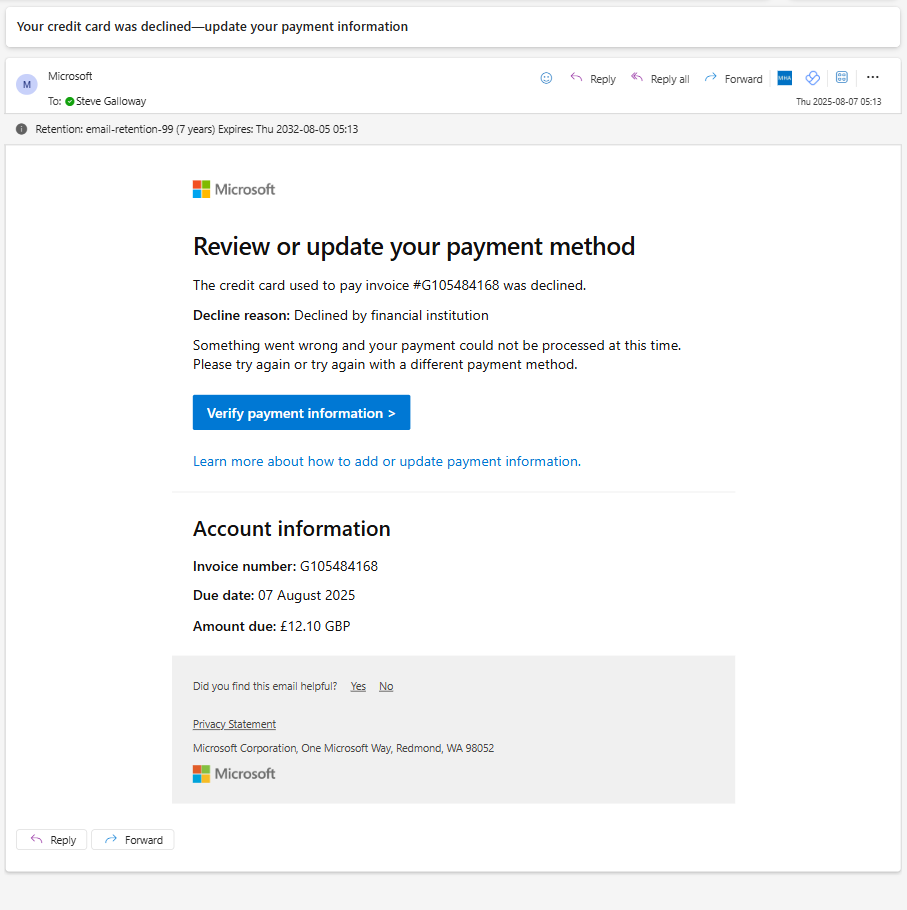
The only way to tell that this evidently legitimate email from Microsoft is a hoax was to hover over the “verify payment information” link to see that the link was not a valid Microsoft end point.
Key tactics include:
- Voice phishing (vishing): Scammers impersonate IT support over the phone.
- CAPTCHA-protected phishing sites: These look legitimate and bypass basic security.
- Crypto wallet scams: Fake alerts trick users into giving up credentials.
Threatlabz goes on to say that even education sectors are under attack, with phishing up 224% in 2024. The goal? Steal data, money, or access to systems.
AI-Powered Fraud: A New Era of Deception
AI is changing the game. It helps scammers build fake websites, clone voices, and create deepfake videos [2]. These tools make fraud faster and harder to detect.
Common scams include:
• Fake job offers: AI-generated listings lure applicants into sharing personal info.
• E-commerce fraud: Entire storefronts are built with fake reviews and products.
• Tech support scams: Attackers pose as IT staff to gain remote access.
Microsoft reports that AI tools are being used to scan the web for company data. This helps attackers create highly personalized lures.
Summary
Customizing folder colours is a great way to help you and others find content easily, especially in large folder lists. Remember, you can also “favourite” a folder to help find your content faster.
Changing a folder’s colour in OneDrive will only be visible to you.
Changing a folder’s colour in Sharepoint will be visible to users who you share it to.
Since Teams stores folders and files in Sharepoint, Teams administrators can change folder colours by opening a Teams’ file library using <View in Sharepoint>.
Lastly, Sharepoint’s broader capabilities means that advanced users can automate folder properties including folder colours.
Business Email Compromise (BEC): The Silent Threat
BEC attacks are rising. These scams involve impersonating executives to request wire transfers or sensitive data according to Socium. AI helps attackers mimic writing styles and internal workflows.
Watch out for:
- Lookalike domains: Slight changes in email addresses trick employees.
- Predictive phishing: AI analyzes past emails to time attacks perfectly.
- Urgent requests: Messages often pressure staff to act fast without thinking.
BEC is costly and hard to detect. It’s one of the most damaging threats facing businesses today.
How to Stay Protected
Cyber threats are evolving, but so are defenses. Here’s how to stay ahead:
- Use multi-factor authentication (MFA) across all platforms.
- Train employees regularly with phishing simulations.
- Deploy AI-powered email filters to catch suspicious content.
- Secure mobile devices against smishing and app-based attacks.
- Consider enhanced security like Conditional Access, which limits access to approved devices.
Zero Trust principles and advanced threat detection tools are key. They help limit damage even if an account is compromised.
Summary
Email threats in 2025 are smarter and more dangerous than ever. AI is helping attackers craft believable scams that bypass traditional defenses. But with awareness, training, and the right tools, businesses can fight back.
It is difficult to explain the catastrophinc effect that a professional hack on a business has. Even with resources that companies like Marks & Spencer have, a well executed hack brings enormous costs and losses to bear. Worryingly, high profile hacks are only the tip of the iceberg – small business statistically bear the brunt of hacks than any other business class. Nor is it business that any IT professional wants to have to take one. Usually, this is because it was avoisdable in the first place. Talk to us first.
About ComStat.uk: Internet Service Provider Comstat provides IT support, web hosting, and media services including web design, Microsoft 365 setup, and audio/video production, serving businesses across Denbighshire, North Wales and Wirral from Ruthin, and Lancashire and the Northwest from Bolton.