by Steve Galloway | Mar 4, 2025
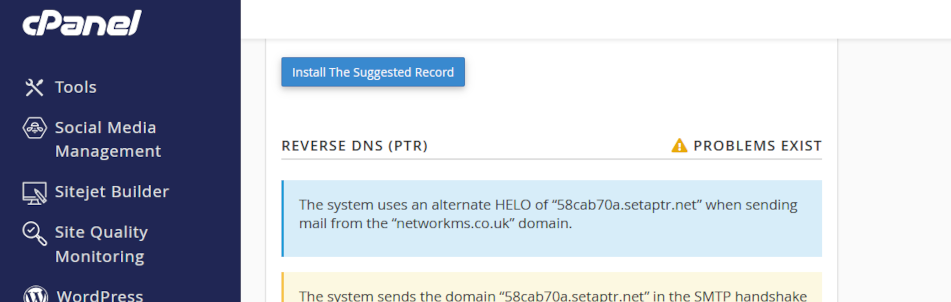
Reverse DNS
Reverse DNS, also called rDNS, is used by email servers to verify that email has arrived from a valid server before allowing incoming email into a network. point. rDNS is crucial for email deliverability and server reputation. For instance, web site contact forms often fail because Reverse DNS is not configured properly and emails are dropped before reaching a web site owner’s Inbox. This is why SPF, rDNS, DKIM, and DMARC are so important in business email.
Folder colours help you pick out important locations in long lists. Also, you can colour-code folders to distinguish between content.
Click on the headers below to follow our guide to record a Reverse DNS/PTR record in your domain name’s zone record at your domain registrar. Click on images to see in full resolution.
How to prepare
If your DNS is managed using nameservers at a domain name registrar, you will need to create a Reverse DNS/PTR record in the zone record where you keep your domain name. If your domain name operates using our nameservers (i.e. ns1.namesfirst.net) you only need to check your zone record in cPanel by pointing to Domains > Zone Editor to determine if a record needs establishing.
Therefore, before you proceed, prepare as follows:
- if in doubt, check with us where your records need modifying
- find your cPanel login credentials from our server information sheet
- (optionally) find the login credentials for your domain name supplier
If you are nervous about dealing with this technology, we can provide admin support for domain names and ongoing services – ask for help.
Step-by-step instructions
This workflow assumes that your domain name is managed at the domain name registrar where you manage and renew your domain name. If you are unsure where your DNS zone is managed, contact us.
1. Understand Reverse DNS:
- rDNS maps an IP address to a domain name
- It’s the opposite of the usual DNS lookup
2. Find out your web server’s IP address:
- your server’s IP address in displayed in your cPanel home page (usually towards upper right)
- make a note of the address
3. Log in to your domain name supplier:
- raise a support ticket asking for rDNS and providing the following:
- the IP address you noted in 2 above
- the PTR value for the PTR field – usually, this would be mail.yourdomain.com
- if your supplier asks for more information – there are a few ways to create this record
- expect up to 24 hours for the record to work
4. Verify rDNS:
- use a resource like MXToolbox to verify your IP address resolves to mail.yourdomain.com
- if necessary, follow up with your ISP
Summary
Reverse DNS is an important tool that remail servers rely on to verify that email you send is recognized as valid. Without this validation, you may send email that is rejected or dropped before it reaches a recipient’s Inbox.
Making adjustments to your domain name’s zone record requires exacting language and syntax. A missing character can cause a web site to cease functioning and disable your organisation’s email. Nor can you test a modification first – changes made have effect in real time.
Expert help available
We have decades of experience managing domain names on behalf of clients. If you are nervous about dealing with this technology, we can provide admin support for domain names and ongoing services. We can turn modifications in minimal time at reasonable cost while saving you from risk of web site and email disruption – please ask for help if in doubt.
by Steve Galloway | Feb 4, 2025
Authenticate your outgoing email with SPF
Use SPF (Sender Policy Framework) is a utility that lists all the server IP addresses that a domain name can use to send emails from.
Click on the headers below to follow our guide to manage SPF record using cPanel WHM and then post your SPF record in your domain name’s zone record at your domain registrar. Click on images to see in full resolution.
Why is SPF important?
Most people who rely on a contact form have experienced what happens when SPF is not working.
For instance, your business might use Microsoft 365 (i.e. Exchange). Exchange handles all staff email and its servers use IP addresses to do so. Now, imagine that your business also has a web site with a contact form but the web site sends contact form email from a different IP address than Microsoft Exchange uses for everyday emails: the contact form uses the web server’s IP address. SPF means your business can validate the web site’s server IP address. Without properly configured SPF, the contact form would not work. You would never know you lost a sale. At best, contact form email might end up in Spam/Junk.
How do I configure SPF?
If your web server is configured for email, you might not need to do anything at all. If you already use another email service for regular email, you may need to amend your existing SPF record where you manage your domain name to include the IP address for your contact form. The best thing to do is to contact us first for advice.
Step-by-step instructions
This guide assumes that you need to create an SPF record at your domain name supplier, but you want to operate your email from our new web server.
1. Log in to cPanel
- using your web server configuration sheet, log into cPanel
- navigate to <Email>
- click on <Email deliverability>
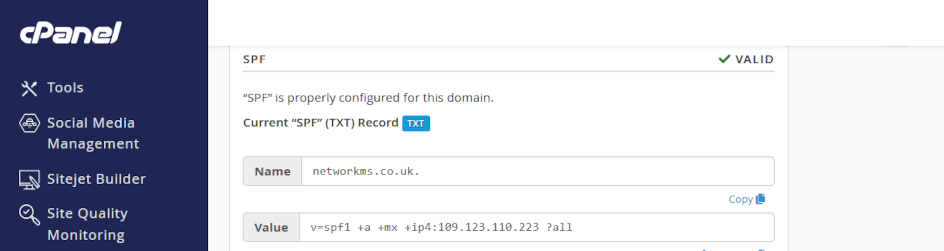
2. Find your SPF record
- towards the top of your page, you will see a section for SPF, like you see in the screenshot below.
- the SPF <value> is the entry you need to modify your existing domain name record where you manage your domain name – copy the record from cPanel.
- go to your domain name supplier

3. Create or edit your SPF record
- log in to your domain name manager or zone editor
- if there is no SPF record, create a new TXT or SPF record, and enter the the values from cPanel
- if there is an SPF record, copy the existing record an paste/save it so you have a last known working state
- if the existing SPF record handles other email alredy, you will need to determine how to add your web server’s IP address to the entry. This is because you use one SPF record to define all IP addresses that need to be covered.
SPF can be the simplest of protocols to implement, especially if you are operating all email from your web server and your domain name uses our nameservers. However, SPF needs to be able to cope with diverse eventualities, and it may need configuring for multiple IP addresses that handle email for your business. If in doubt, contact us for advice.
Summary
SPF is already configured if your web server includes email services, so there is nothing to do if we manage your domain name for you and all your email will be handled from your web server.
In most other cases, you should contact us for guidance before you make changes anywhere. If you do make changes to existing records, be sure to copy/paste/save those records so that you can resort to a last known working state if problems develop.
DNS is not a forgiving technology, and if you are nervous about making real time changes that might disrupt your web site and/or email, please contact us at the very least for advice.
Expert help available
We have decades of experience managing domain names on behalf of clients. If you are nervous about dealing with this technology, we can provide admin support for domain names and ongoing services. We can turn modifications in minimal time at reasonable cost while saving you from risk of web site and email disruption – please ask for help if in doubt.
by Steve Galloway | Mar 27, 2024
Office 365 help series – Changing passwords using OWA
Password security
It is good practice to change email passwords occasionally. Sometimes, ComStat may ask you to change passwords if we suspect that a third party has compromised your account. If you have forgotten your password, we can force a password change.
Users are responsible for their passwords at all times. If we force a password change, users should log in to their email accounts and overwrite forced password changes with passwords of their own. Good passwords include:
- 8-15 characters
- Capital letters
- Numbers
- Special characters
Email passwords cannot be changed using your desktop version of Outlook. To change your email account password, login to your Office 365 online control panel with your email address and existing password with a web browser like Internet Explorer, Firefox, or Chrome.
There is more than one way to change passwords in Office 365. For instance, users can log into http://portal.office365.com and locate settings from the portal home page. Users are familiar with Outlook Web Access, so the tutorial here should be a convenient method.
Read this article first before you begin. Click open each step below to understand the steps you need to follow. If you need to contact us to force a password for you, get in touch with your usual network administrator or contact us using the information on our contact page.
Office 365 Home Page
Using your web browser, login to Office 365’s control panel at http://mail.office365.com. Login with your email address and existing password. Your Office 365 home page looks like this:

Open OWA settings
Click open the settings icon on the right side of the toolbar at the top right corner of your screen. The seettings icon looks like a cog.
Change password
Follow the 3 steps in the illustration below:
- Click open Office 365 settings
- Click on Password
- Change your password and click submit in the last screen

Remember, you need to know your old password to create your new password, so you may have to ask us to force a password change for you. Also, changing your password will mean you need to update settings on any devices that connect to your Office 365 account, including desktops, laptops, tablets, or mobile phones. Lastly, you may be asked to authenticate your password change by verifying your mobile phone number and inputting a short code which your server will text you, so your mobile phone should be available.
by Admin | Sep 1, 2023
With effect from September 1st, ComStation.co.uk is providing support network administration for EOP security tools for email.
EOP (Exchange online Protection) is a Microsoft solution for managing virus, spam, phishing and other malicious formats. Critically, the service is managed at the data centre for incoming AND outgoing email. Managing incoming email in this way reduces the risk of contaminated email reaching users’ machines.
Microsoft estimates that over two thirds of email transiting the Internet is junk, spam, or malicious. In the field, ComStat devotes significant time to repairing customer equipment compromised by users inadvertently opening suspect email.
EOP includes control panels for customising filtering, IP blocks, domain name blocks, and more. EOP also integrates with ComStation.co.uk tools for data leakage protection, enabling organisations to manage senstive information in outgoing email which might include regulated personal data, credit card numbers, other company information, etc. Invoking data policies in thi way helps organisations to educate employees. Systems can be configured to allow users to override system recommendations while logging user decisions, and also unilateral suppression of sensitive information (e.g. credit card numbers, passwords, etc.)
EOP does not manage over PC security, however is a game changing solution for end users because it minimizes risk of costly damage to buiness networks and machines. Also, because the security process is managed at the data centre, ComStat is able to deliver “clean” email not only to user workstations, but also to the user’s connected devices like mobile phones, laptops and tablets.
EOP was orginally developed to support Microsoft Exchange, and is more than anything else specialised software that deals with email. In this respect, EOP’s email protection services are often more comprehensively tooled than conventional Anti Virus applications, and is used widely by the world’s largest businesses.
EOP is included in ComStat’s subscription email services for business users. EOP can be provided as a standalone solution (£2.00/mo per user account, £20.00 annual) for services provided by third party data centres.





