by Steve Galloway | Feb 4, 2025
Authenticate your outgoing email with SPF
Use SPF (Sender Policy Framework) is a utility that lists all the server IP addresses that a domain name can use to send emails from.
Click on the headers below to follow our guide to manage SPF record using cPanel WHM and then post your SPF record in your domain name’s zone record at your domain registrar. Click on images to see in full resolution.
Why is SPF important?
Most people who rely on a contact form have experienced what happens when SPF is not working.
For instance, your business might use Microsoft 365 (i.e. Exchange). Exchange handles all staff email and its servers use IP addresses to do so. Now, imagine that your business also has a web site with a contact form but the web site sends contact form email from a different IP address than Microsoft Exchange uses for everyday emails: the contact form uses the web server’s IP address. SPF means your business can validate the web site’s server IP address. Without properly configured SPF, the contact form would not work. You would never know you lost a sale. At best, contact form email might end up in Spam/Junk.
How do I configure SPF?
If your web server is configured for email, you might not need to do anything at all. If you already use another email service for regular email, you may need to amend your existing SPF record where you manage your domain name to include the IP address for your contact form. The best thing to do is to contact us first for advice.
Step-by-step instructions
This guide assumes that you need to create an SPF record at your domain name supplier, but you want to operate your email from our new web server.
1. Log in to cPanel
- using your web server configuration sheet, log into cPanel
- navigate to <Email>
- click on <Email deliverability>
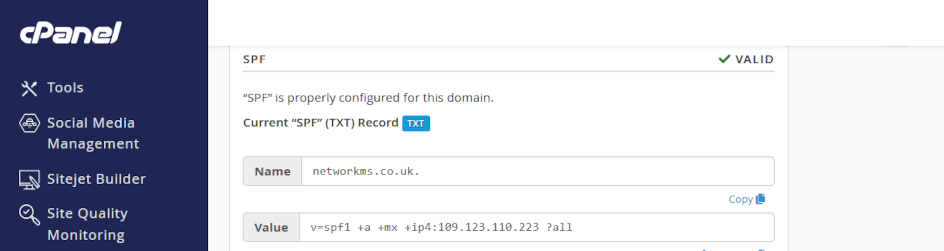
2. Find your SPF record
- towards the top of your page, you will see a section for SPF, like you see in the screenshot below.
- the SPF <value> is the entry you need to modify your existing domain name record where you manage your domain name – copy the record from cPanel.
- go to your domain name supplier

3. Create or edit your SPF record
- log in to your domain name manager or zone editor
- if there is no SPF record, create a new TXT or SPF record, and enter the the values from cPanel
- if there is an SPF record, copy the existing record an paste/save it so you have a last known working state
- if the existing SPF record handles other email alredy, you will need to determine how to add your web server’s IP address to the entry. This is because you use one SPF record to define all IP addresses that need to be covered.
SPF can be the simplest of protocols to implement, especially if you are operating all email from your web server and your domain name uses our nameservers. However, SPF needs to be able to cope with diverse eventualities, and it may need configuring for multiple IP addresses that handle email for your business. If in doubt, contact us for advice.
Summary
SPF is already configured if your web server includes email services, so there is nothing to do if we manage your domain name for you and all your email will be handled from your web server.
In most other cases, you should contact us for guidance before you make changes anywhere. If you do make changes to existing records, be sure to copy/paste/save those records so that you can resort to a last known working state if problems develop.
DNS is not a forgiving technology, and if you are nervous about making real time changes that might disrupt your web site and/or email, please contact us at the very least for advice.
Expert help available
We have decades of experience managing domain names on behalf of clients. If you are nervous about dealing with this technology, we can provide admin support for domain names and ongoing services. We can turn modifications in minimal time at reasonable cost while saving you from risk of web site and email disruption – please ask for help if in doubt.
by Steve Galloway | Aug 20, 2024
1. What Is Inline Archiving in Microsoft 365?
Inline archiving in Microsoft 365 is a feature designed to help users manage large volumes of email. It provides an additional mailbox—called the archive mailbox—where older messages can be stored automatically or manually. This helps keep your primary mailbox uncluttered and improves performance.
This feature is especially helpful. You do not need advanced skills to use it, and inline archiving works seamlessly with Outlook and Outlook Web App. Once enabled by your organization’s IT admin, you’ll see an “In-Place Archive” folder in your mailbox. You can move emails there manually or set up rules to do it automatically.
Click open the headers below to learn how to use Microsoft 365 inline archiving to manage emails, automate archiving, and keep your mailbox clean—even in the archive.
2. Why Inline Archiving Is Useful
Managing email can be overwhelming, especially when your inbox grows quickly. Inline archiving helps by:
- Improving performance: A smaller mailbox loads faster
- Reducing clutter: Older emails are moved out of your main inbox
- Supporting compliance: Archived emails are stored securely and can be retained according to company policies.
For organizations with strict data retention rules, inline archiving ensures that emails are preserved without taking up space in the active mailbox. It’s a win-win for both users and IT departments.
3. How to Automate Archiving in Microsoft 365
To make archiving easier, you can set up automatic rules. This is how to do it:
- Use Retention Policies: These are set by your IT admin or global administator and can automatically move emails older than a certain age to the archive mailbox
- Manual Setup in Outlook:
- Right-click on a folder and choose Properties
- Go to the Policy tab
- Choose a retention policy that moves items to the archive after a set time (e.g., 6 months)
- Use Sweep Rules in Outlook Web App: Sweep is a terrific innovation to move emails from specific senders like newsletters, or with emails that you can indentify with certain keywords, to the archive
Establishing a routine means checking your inbox weekly, archiving emails you no longer need immediately, and letting automated rules handle the rest. This keeps your mailbox tidy without constant effort.
4. Managing Your Archive: Why Deletion Still Matters
Even archived emails can pile up over time. Subject to your organization’s data retention policies, it’s important to manage your archive just like your inbox.
This is what you can do:
- Review old content: set a reminder every few months to check your archive
- Delete outdated emails: iIf your company allows it, remove emails that are no longer needed.
- Use retention tags: retention tags can be applied to archived items to automatically delete them after a set period.
Summary
Imagine letting your morning postal deliveries pile up on the kitchen table for 15 years – who would do that? Yet that is what we do with our email. Without management, we suffer from slower access to ever increasing data volumes, and we risk exposing data to breaches which could breach data protection policies. So, managing our spent email is an important habit.
Remember, archiving is not the same as permanent storage. Keeping your archive clean helps with compliance, improves search speed, and ensures you’re not holding onto unnecessary data.
About ComStat.uk: Internet Service Provider Comstat provides IT support, web hosting, and media services including website design, Microsoft 365 setup, and audio/video production, serving businesses across Denbighshire, North Wales and Wirral from Ruthin, and Lancashire and the Northwest from Bolton.
by Steve Galloway | Mar 27, 2024
Office 365 help series – Changing passwords using OWA
Password security
It is good practice to change email passwords occasionally. Sometimes, ComStat may ask you to change passwords if we suspect that a third party has compromised your account. If you have forgotten your password, we can force a password change.
Users are responsible for their passwords at all times. If we force a password change, users should log in to their email accounts and overwrite forced password changes with passwords of their own. Good passwords include:
- 8-15 characters
- Capital letters
- Numbers
- Special characters
Email passwords cannot be changed using your desktop version of Outlook. To change your email account password, login to your Office 365 online control panel with your email address and existing password with a web browser like Internet Explorer, Firefox, or Chrome.
There is more than one way to change passwords in Office 365. For instance, users can log into http://portal.office365.com and locate settings from the portal home page. Users are familiar with Outlook Web Access, so the tutorial here should be a convenient method.
Read this article first before you begin. Click open each step below to understand the steps you need to follow. If you need to contact us to force a password for you, get in touch with your usual network administrator or contact us using the information on our contact page.
Office 365 Home Page
Using your web browser, login to Office 365’s control panel at http://mail.office365.com. Login with your email address and existing password. Your Office 365 home page looks like this:

Open OWA settings
Click open the settings icon on the right side of the toolbar at the top right corner of your screen. The seettings icon looks like a cog.
Change password
Follow the 3 steps in the illustration below:
- Click open Office 365 settings
- Click on Password
- Change your password and click submit in the last screen

Remember, you need to know your old password to create your new password, so you may have to ask us to force a password change for you. Also, changing your password will mean you need to update settings on any devices that connect to your Office 365 account, including desktops, laptops, tablets, or mobile phones. Lastly, you may be asked to authenticate your password change by verifying your mobile phone number and inputting a short code which your server will text you, so your mobile phone should be available.
by Admin | Sep 1, 2023
With effect from September 1st, ComStation.co.uk is providing support network administration for EOP security tools for email.
EOP (Exchange online Protection) is a Microsoft solution for managing virus, spam, phishing and other malicious formats. Critically, the service is managed at the data centre for incoming AND outgoing email. Managing incoming email in this way reduces the risk of contaminated email reaching users’ machines.
Microsoft estimates that over two thirds of email transiting the Internet is junk, spam, or malicious. In the field, ComStat devotes significant time to repairing customer equipment compromised by users inadvertently opening suspect email.
EOP includes control panels for customising filtering, IP blocks, domain name blocks, and more. EOP also integrates with ComStation.co.uk tools for data leakage protection, enabling organisations to manage senstive information in outgoing email which might include regulated personal data, credit card numbers, other company information, etc. Invoking data policies in thi way helps organisations to educate employees. Systems can be configured to allow users to override system recommendations while logging user decisions, and also unilateral suppression of sensitive information (e.g. credit card numbers, passwords, etc.)
EOP does not manage over PC security, however is a game changing solution for end users because it minimizes risk of costly damage to buiness networks and machines. Also, because the security process is managed at the data centre, ComStat is able to deliver “clean” email not only to user workstations, but also to the user’s connected devices like mobile phones, laptops and tablets.
EOP was orginally developed to support Microsoft Exchange, and is more than anything else specialised software that deals with email. In this respect, EOP’s email protection services are often more comprehensively tooled than conventional Anti Virus applications, and is used widely by the world’s largest businesses.
EOP is included in ComStat’s subscription email services for business users. EOP can be provided as a standalone solution (£2.00/mo per user account, £20.00 annual) for services provided by third party data centres.
by Admin | Jan 21, 2023
From October 1st ComStat can provide support to help organisations and users manage data leakage and data protection.
On a large scale, data leakage is a serious issue which finds its way into national headlines. American retailer Target faced enormous losses and serious reputational damage in November 2013 when the company lost 40 million credit card numbers to hackers.
Small businesses may argue they do not face such risks, however small businesses are subject to the same data protection governance for due diligence regarding personal information, and even if a small business does not store credit card numbers electronically, users can still “leak” senstive date to third parties that can come back to haunt businesses.
ComStat network administrators have access to a large array of geographically relevant “policies” which can be established monitor outgoing email for sensitive information like credit card numbers, drivers licenses, passwords, in fact just about anything. On identification of an imminent “leak” users are notified with a number of options:
1. Users can override and permit transit of email, although the event is logged,
2. Sensitive information can be masked by the system,
3. Sensitive information can be delted,
4. Entire emails can be deleted with user notification.
ComStat’s engineers work with businesses with a strategy of using these kinds of tools to educate users of risk while enabling them to conduct their business with minimal obstruction.
In addition to monitoring email textual content, services also extend to identify attachments, which might comprise forms like applications, patents, etc.
Data leakage and data protection issues are difficult to meaasure because the risk of loss is usually hard to quantify until a significant event, by which time businesses can be exposed to substantial threat. As a lowest common denominator, however, businesses have an strict obligation to protect customer and third party personal information, and increasingly free email services like GMail, Yahoo, and Live do not provide tools to manage with the responsibilities European and UK law impose on businesses.
Although these services are aimed primarily at ComStat’s Exchange email users, the same tools are being expanded in 2014 and 2015 to encompass raw data storage like document libraries, spreadsheets, pdf’s, etc.
Please contact us to find out more about how our data protection services can help you.



